Our last blog post on this subject introduced the cloud, and some of the advantages that it can bring to your business.
Also, on a side note, migrating and using the cloud to house your IT infrastructure does ensure a much better level of security than having it on premises.
Even with using the cloud, however, there are some security vulnerabilities that need to be addressed, and the use of biometrics can help in this regard.
In this blog post, we review the first layer of the Cloud, the “Infrastructure as a Service”, or the “IaaS” for short, and how Biometrics can be used to further protect it.
The IaaS
As its name implies, the IaaS provides the framework or the foundation from which all of the IT assets and IT resources can be leveraged towards the end user, whether it is a business or a corporation, or even just an individual.
An example of an IaaS platform is illustrated below:

The IaaS, in particular, includes the hardware, network connectivity, all of the software applications (which includes for example, all of the VoIP applications, E-Mail applications, database applications, software development applications, etc.) as well as the other “raw” tools which help to comprise this infrastructure.
So as one can see from the above description, the IaaS platform is literally stored in physical servers, and then it’s partitioned off into instances of virtual servers that each end user will have of their own.
How Can Biometrics Be Used to Protect the IaaS?
Since these servers are stored in large data centers, having superior levels of secure physical access entry points is key.
At the current time most of the security measures that are used to protect the rooms in which the IaaS servers are stored in – make use of smart cards, ID badges, using a secure FOB, etc.
However, these have their inherent security weaknesses.
For instance what if any of these mechanisms are lost or stolen, or worse yet, what if another employee gives out their credentialing tools to another employee so that they can gain access as well, when they are not supposed to?
In these instances, you need a device which not only lets just authorized users to enter the area in which the IaaS resides in, but can also 100% confirm their identity as well.
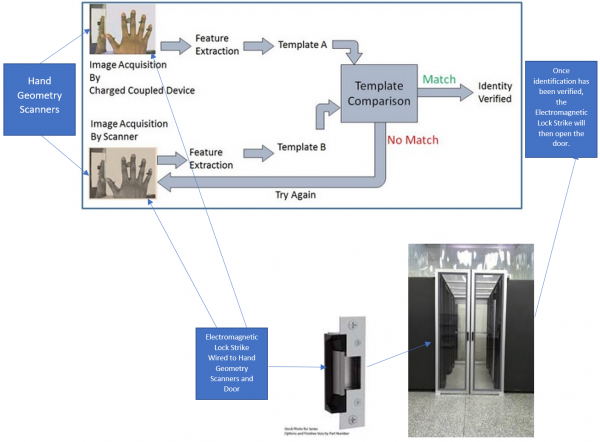
Probably the best suited tool for this situation is the hand geometry scanner, which is illustrated below:

From here, the end user (which is typically the employee), would align their hand into the pegs, which is outlined in the picture.
This can also be further depicted in the below illustration:

At this point, over 96 measurements of the hand are taken in a rapid, successive fashion.
From there, the raw image is compiled, and the unique features are then extracted.
This same process is used to compile both the enrollment and verification templates.
So if an employee wants to gain access to the secure area which houses the IaaS servers, he or she would have their hand scanned, in a process that takes under two seconds.
If there is enough statistical correlation between the two templates as just described, the employee is allowed access to the IaaS servers.
It should be noted that the hand geometry scanner would be wired to an electromagnetic lock strike, and upon successful identification of the employee, this lock strike would then automatically open the door for the employee to enter into. This is illustrated in the diagram below:
Conclusions
Our next blog will examine how biometrics can be used to protect the next layer of the cloud, which is the “platform as a service”, or “PaaS”.